Our Blog

Deliverables of pen-testing
Structure and content of a pen-testing progress status update The pen-testing project is initiated, the requirements including the testing-environment are agreed and the pen-testing team has started...
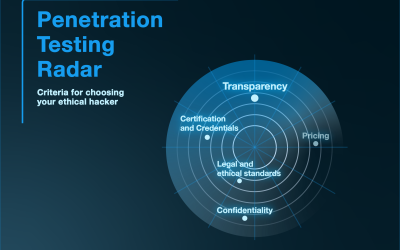
In ethical hackers for pen-tests we trust
When it comes to improving the IT security environment, pen-testing serves as a major tool to identify possible threats and vulnerabilities without an immediate negative impact on the business. Ethical hackers, also known as white-hat hackers, are cybersecurity...
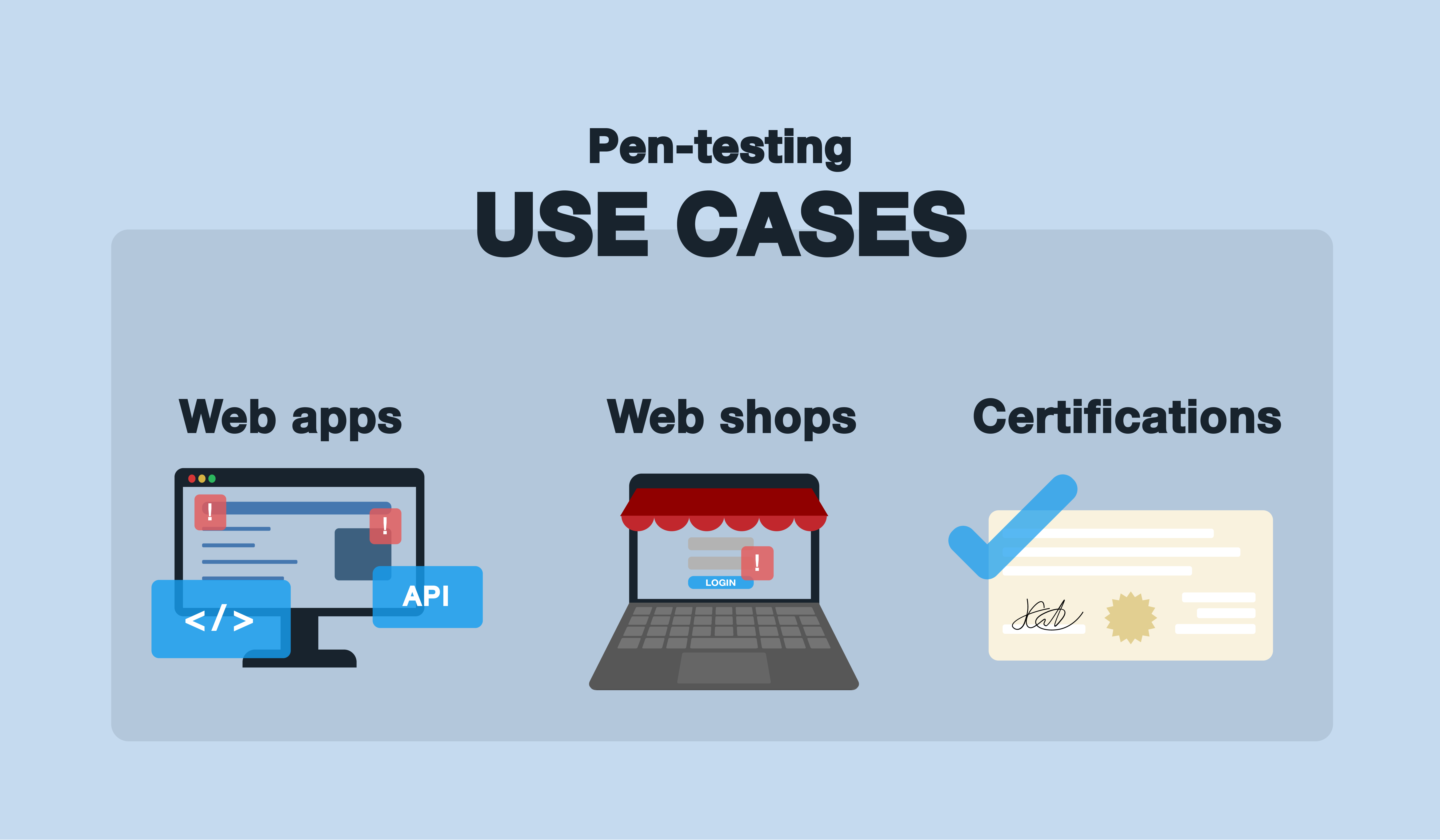
Typical use cases of pen-testing utilization
Companies consider cybersecurity as the number 1 priority topic when it comes to taking business risk management measures, as outlined, for example, in the most recent risk barometer report from Allianz. How did the businesses without extensive internal cybersecurity...
Maximize the value of pen-testing
With our experience gathered in multiple customer projects we observed multiple times a huge value potential for businesses utilizing pen-testing services for their cybersecurity targets. While executing software development or standard software integration projects...
Contact
eudaiTec GmbH
Siegfriedstr. 19
13156 Berlin